My career has been in Information Technology for a long time now, and I absolutely love what I do. Every day is different, every challenge is a new one, and it’s a career that has endless possibilities. I also find that it’s unique and incredibly complex.
You see, technology is not many people’s strong suit. While we all use it every single day, many people just don’t fully understand how it all works. All they know is that it works.
Having such vast know-how in how technology works, especially for consumer devices, I offer my personal time and expertise for free. I tell people all the time that I want to help them fix their problems and will make myself available to do so.
Online forums, remote desktop connections, and showing up at their houses, I enjoy helping people with their technology woes and even sharing knowledge so that they can fix it on their own in the future.
As such, I was at work, and a coworker asked me a question that I’ve been getting a lot lately. They asked me “how do I stay more secure online?”
It’s a reasonable question and a question that a lot of people should start asking. Every time we grab our phones or computers, we connect to the World Wide Web, and there are plenty of people out there that want to track us.
I’m not talking about individual internet stalkers, that is a topic for a different day, but rather trackers who track millions of people every day as they browse the web.
How many times have you said a product that you’ve been talking about buying in a discussion with a friend, shows up in an advertisement on Facebook or Instagram?
Internet Service Providers, search engines, advertisers, and governments are the trackers that I am talking about today and those who look to take your personal information online, and either profit from it or follow you to make sure you are behaving.
Today, I am going to go over a new way of maintaining security, one that does not compromise on functionality. I enjoy Facebook, Instagram, my Android phone, the Windows 10 operating system, browsing the web, and the lot of it. I don’t want to give any of that up.
Therefore, my goal here is to introduce a way to lower the amount of tracking that happens in your digital life. While there are plenty of ways of eliminating it and becoming anonymous online, that isn’t much of a life.
Below are steps to beef up your own internet security, decrease internet tracking, and feel safer while browsing the web without compromising how you use the web or your devices.
What are they tracking? Who are they?
You are valuable. You are worth a lot, for a lot of different reasons to a lot of different people. The value that I speak of today is the value that you browse the online web, and you shop online.
Unless I am driving, sleeping, or talking to someone, I’m probably online doing something. While online, I may read the news, search on Google, look at memes, or go shopping for something. All of that is valuable to the right company.
Companies are the first trackers of the internet.
Amazon, eBay, Walmart, Target, and the rest of the eCommerce websites all want to know how you shop online. By knowing how you shop online and what you look for when searching for something, they can begin to offer you product recommendations.
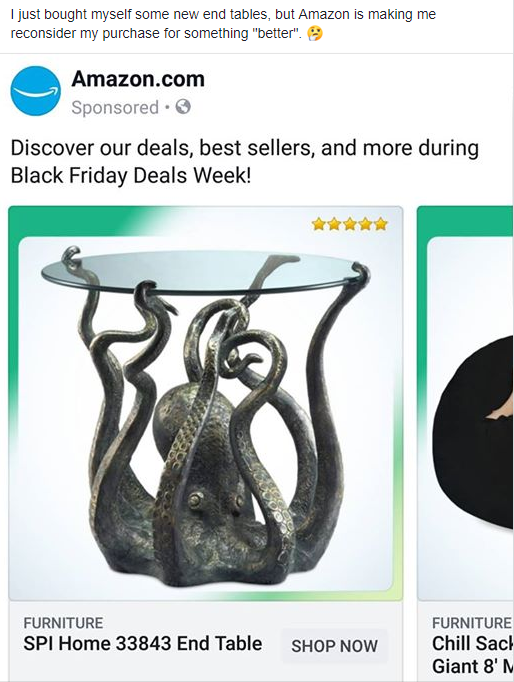
For example, before I had moved into my apartment, I was on the hunt for some end tables for my couch. I searched Amazon, Wayfair, Google, and a whole lot of online stores. I couldn’t find exactly what I wanted, so I stopped my search. Eventually, I bought a full set from Wayfair.
However, Amazon knew that I was looking for end tables. They hadn’t known that I had purchased any, just that I was looking. A few days after my Wayfair purchase, I posted this on Facebook. It’s a screenshot of Amazon’s recommended products to me based on my interest.
Even though it’s a strange end table, it’s a recommendation based on my shopping history. That is one of the hundreds of examples that show that Amazon is following me online and then recommends.
Stories like this date way back before the mainstream internet. Once upon a time, a father was angry at Target for sending his daughter physical product catalogs and showcasing baby cribs and baby items to his daughter. The father called Target to complain at how they were sending such catalogs to his daughter who, he thought, wasn’t pregnant.
You see, his daughter was pregnant, and she had yet to tell her father. Target, however, knew based on her search results online. Results that they bought.
While eCommerce companies want to buy your data, they aren’t the only companies out there that are the problem. Virtually every company is the problem.
Facebook, Google, Microsoft, Apple, Twitter, they all collect every single thing you do on their website and their products.
Facebook knows who you talk to the most and who you like more than others. Google tracks your interactions with different websites and your searching results. Microsoft collects user data from its operating systems. And so on.
As such, these companies grow to such a gigantic size because they are advertisers, the second trackers on the internet.
Advertisers are certainly different from companies. Google is a perfect example of this situation. Google, with their massive amounts of data collection, does not sell your data. They state so in their privacy policy. Instead, they sell you as a person.
I have advertised for Qwerty Articles before using Google and Facebook, both of which ask me certain questions such as customer target age, race, political views, and career background. Then, they take my advertisement and show it to those people.
Google or Facebook never give me their user’s data. They instead take my advertisement and show it to the people I want to show it to, to maximize my click count.
Therefore, instead of companies like Amazon, who track what you do on the internet, advertisers track who you are. They want to know as much about you as possible so that they can show you personalized advertisements which have a far better chance of you clicking on them.
Next, there is your Internet Service Provider (ISP). This is the group that serves you your actual internet connection.
Being the gatekeepers of your internet, it shouldn’t be a surprise that they can see everything you do. Your ISP isn’t a huge tracker per se. They don’t know what you do on a website, just which websites you are connecting to.
Unlike a company that can only track you on a website where it has listeners, your ISP connects you to every single website and with that knows your every move while browsing the web.
We will talk later on with masking the amount of information you send to your ISP.
When it comes to the government, it all depends on which government we talk about. The Chinese government nearly accomplished a complete data take over of the United States and its citizens with their recent 5G attempted takeover.
Their goal was to control the US 5G wireless network and with that report back all of the data to China. Furthermore, the Chinese government was found to have illegally tampered with server equipment in companies such as Apple and Amazon that too reported information back to China.
Both instances were stopped by the Trump Administration, but that doesn’t ignore the fact that a government is spying on its people.
In the United States, government internet tracking is done through warrants, data seizes, and when tracking down illegal internet activities.
The US government doesn’t spy on its users per se, but when the time comes will rather ask companies that do spy to provide all of their data on an individual, essentially allowing the government absolute tracking rights.
They can utilize the law and ask for any information that they wish to have and do as they please with it, making them the worse tracker of them all.
Technically speaking, the government tracks you outside of the internet. Living in Wisconsin, if I drive down to Illinois, there are toll roads with cameras on them. Those cameras will take a picture of your license plate and then track you as you down the road. They know when you get on the highway and when you get off.
In Europe, cameras track you in the car to ensure that you are driving your car and that you aren’t texting and driving or even sleepy.
Browsing the Web
We are our own downfall when it comes to giving out information. Every time we sign up for a new website, we volunteer our names, addresses, and much more as if we know the website personally.
Plenty of people tell Facebook all the information that they need to know to advertise to you. We give them our full name, phone numbers, home town, birthday, and a whole lot more. And this isn’t particularly bad to do.
The first step in protecting your digital life is to consider the amount of information you volunteer. For example, when creating a new online account, do you really need to give your full name? If you aren’t buying anything, perhaps only provide your initials or your first name and the first initial of your last name.
You could even go a step further, and for accounts that you don’t care much for, you could consider using an alias as I do on my Gmail account. That way, when I send an email from Gmail, it doesn’t broadcast my real name to every receiver. I often use this for when registering for sites I won’t use often.
Now, the major leak for your digital life is your browser. Chrome, Firefox, Edge, they are all personalized to you, and your browser is like a digital fingerprint. Every time you visit a web page, your browser voluntarily sends information about who you are to that website.
Your location, browser version, add-ons, screen size, operating system, and much more. You can see what your browser sends to websites here.
Chrome is the worse browser you could use if you are concerned about privacy, yet I use it as my browser. As far as data collection goes, Firefox would be my recommendation as they collect very little to no personal information from their users.
Chrome, on the other hand, will report back all of your doings to the mothership. You can’t get around that, but what you can get around is how much other websites collect on you.
Whether you are using Chrome or Firefox, there are some fantastic tools to help protect you while browsing online.
The first is uBlock Origin. This is essentially an adblocker that will stop nearly all ads from tracking you and remove them from your web browsing experience. Additionally, it even blocks ads on YouTube and other streaming platforms.
Next, take a look at Privacy Badger. It works well with uBlock, and while it may have a lot of overlap with uBlock, it stops websites and trackers, such as Google, from following you across the internet.
Then for security purposes, HTTPs Everywhere is an excellent way to force your internet traffic to be encrypted. This isn’t as important at home, but if you are browsing the web on the go, then encrypted network traffic will prohibit hackers from intercepting your internet use.
After installing those three extensions, you may notice that your browser will get faster. Since you no longer need to load a website’s advertisements and trackers, the website should respond and work a ton faster.
Also, don’t worry about websites not working at all because you block the ads or trackers. Rarely does a website stop their users from visiting because of the adblock or does the website cease to work with these tools.
Speaking of such, be careful of which extensions you add to your browser. Some extensions can change data on a website, capture your login credentials, or even display advertisements.
I am very worried about which extensions I am using on my browser. I stick to extensions that are all open sourced, backed by a business, or have limited access to what I do on my browser. Any extension could easily spy on you or take your personal data.
Password Manager
With so many accounts on the internet, it gets difficult to track a password for each one. Many of us, me included, reuse the same password for multiple accounts. We can’t write down each and every password, and if they are too complex, then we can’t remember them.
Nowadays, there are password managers to help us keep unique and complex passwords while remembering one master password.
The purpose of a password manager is to not know your passwords. Weird, I know, but with your one master password, this unlocks your vault of unique passwords associated with all of your accounts. For example, your Facebook account password may be LJRg^jUsX?e#v6@^ and your Google password may be ?P6BknHCC%hJ:Vb-. By making this password super complex, it makes it impossible for a hacker to guess and takes years for a computer to figure out.
You stay secure all while keeping your password unique and different amongst all of your accounts.
There are a lot of password managers available, some that are local and others that are cloud-based. There are paid solutions and free ones, but I use 1Password, which is included in my eero Plus subscription.
I love my 1Password password manager. So much so that I wrote an in-depth review on how it works and why you should consider it.
You can check to see if your password has never been found in a password breach here.
Regardless of your chosen password manager, you want to make sure you aren’t reusing passwords, and you can use a password that is secure, hard to guess, and stored somewhere that you won’t forget. You can even go the additional mile by setting up two-factor authentication on your account to add another layer of security.
Virtual Private Network (VPN)
Just the other day, I was telling a friend how my back had been bothering me during the day. A few minutes passed by, and I went on my smartphone to check Facebook. Lo and behold, what do I discover? A new advertisement for a chiropractor.
Not only was it for something that I was just talking about, but it was a local advertisement. Google had tapped into my smartphone’s microphone, recorded what I said, translated it, and then sold that information to Facebook.
Now, this isn’t a malicious act, but it can be seen as spyware. Watch how Fox News was able to find out that an Android smartphone tracked your location even when the phone had no connectivity and was even set to airplane mode.
It’s creepy, and it makes my skin tingle thinking that a large corporation is watching and listening to my every move. Unfortunately, there isn’t a whole lot you can do about it unless we give up using our smartphones and computers and I can’t see that happening anytime soon.
What you can do is choose to encrypt all of your network traffic as well as appear as if you are connected to another location.
By doing so, your traffic can’t be spied on by internet service providers; those monitoring a network you are connected to will think you are somewhere else in the world. It is a method of anonymizing your traffic.
A virtual private network (VPN) is a tool that encrypts all network traffic, deidentifies it, and can even make it appear as if you are connected to an internet service provider in London when you are actually located in Chicago.
On a secured, no-logging VPN, nobody can follow you on the internet. Not a government, not your internet service provider, and most times, not even the VPN provider themselves.
If you start identifying yourself while on the VPN, such as logging into accounts or sharing personal information, then they will be able to know your IP and learn who you are. However, the moment you drop the VPN connection and reconnect to the VPN, you will have a new IP and become a new person.
A VPN is like a secure tunnel where you are walking to your destination. Without this tunnel, a government, a website, or your internet service provider will know where you are headed.
With a VPN activated, your traffic becomes encrypted, meaning only you and the VPN service provider knows what you are doing on the internet. Essentially, your encrypted traffic leaves your computer, goes to your ISP (who cannot view the data), transfers the internet request to the VPN service provider, and then they move the request to the website you are visiting.
Your ISP will only know that you are using a VPN, not what you are doing on it or where in the web you are going. And, as I said, with a VPN service that does not log its users, you become anonymous.
I use NordVPN as it is one of the largest and highest rated VPN providers on the market. I can connect to basically any country, using multiple different ports such as double VPN, and even select a specific server dedicated for more protection.
There are a lot of VPN companies to choose from but opt for one that specifically states that they do not log any of their traffic and is stationed in a country that does not require logging to be done. NordVPN’s headquarters is in Panama, which exempts them from even the US government.
Be wary of VPN providers who are stationed in the US or have a parent company in the US. They will need to log their users and provide it to the US government if requested by law. Also, stay away from smaller VPN services as they may not be all that they seem.
Antivirus
An antivirus is a tool that scans files and applications on your computer to check their signatures and coding. It understands the difference between good and bad files by receiving daily definition signatures that are provided by the antivirus manufacturer. Depending on the installed antivirus, there could be tens of hundreds of signature updates per day.
Being free and included with all Windows 10 machines, Defender is a powerful antivirus that picks up nearly all popular and most unpopular attacks. In the latest Windows 10 build, it even received the ability to detect ransomware and gets definition updates through Windows Update.
For 90 percent of users out there, Microsoft’s Windows 10 Defender antivirus is the best option. It provides strong protection, covers all sorts of malware, and even has new features like stopping ransomware from accessing user folders.
I used Defender for a long time but eventually made the switch to a paid solution. The paid antivirus solutions offer more features, such as stopping your browser from accessing phishing websites, providing a special browser for banking, and ransomware file protection, than the free alternative. Moreover, their virus definitions are updated more frequently with more signatures to stop more types of attacks.
My first switch to a paid antivirus was to ESET Smart Security Premium. It has all of the bells and whistles previously mentioned and has a modern interface with a strong protection level. It would sometimes interfere with gaming, but a few setting adjustments later resolved that problem.
Overall, ESET was an excellent, paid antivirus solution. One of the neat aspects of ESET is their LiveGrid. It records malicious attacks on all of their client’s computers to help it better understand what malware does and how it got there. They can then respond faster to those attacks by taking this knowledge and updating everyone at once.
When my yearly renewal arrived, I decided to shop around and give Bitdefender a try. With a new deal providing a locked in one-time price for two years and unlimited installs for all of my devices, it was a deal that I could not give up.
Again, it has all of the bells and whistles. This time, having an even more friendly and better interface than ESET. A built-in VPN, protection browser, and strong protection are all included with this too.
For the past six months, I have been using Bitdefender and haven’t had one gripe about it. I’ve turned some of the protection off such as the web URL checker as I found it annoying, but I would rather have an antivirus that is overprotective than under protective.
It shouldn’t matter much which antivirus you eventually settle on but stick with a solution you trust and has a known-name brand behind it. Outside of Microsoft’s Windows Defender, I wouldn’t recommend any other free solutions, and a paid solution is great, but don’t overspend.
If you are using a Mac and take Apple’s word that “Mac’s can’t get viruses”, then you are going to have a sad face when your Mac falls victim to an attack. Macs can certainly get malware. However, it is less common as most Mac applications are downloaded from the App Store, which is scanned by Apple.
An antivirus suite is still recommended for Mac users if you wish to protect yourself while online. If you currently lack one, there is nothing but your browser to protect you from phishing attacks or malicious downloads.
Almost exclusively, Malwarebytes is an antimalware tool that protects millions of computers against new malware attacks. There are other options to choose from for antimalware, but Malwarebytes really owns this market.
Something to note is that an antimalware tool does not replace your antivirus. Having Malwarebytes installed on your computer may protect you from more recent attacks, but their definition signature updates may not include older attacks, and it could slip by the antimalware tool.
Having two antiviruses does not double your protection. One antivirus should be installed on your computer at any given time, or the secondary antivirus should be disabled. Having two antiviruses could cause them to conflict with one another or be a performance hog on your system.
Common Sense
You can have the best antivirus, the best antimalware, with an updated browser, and be as careful as you can on the internet, but the truth is that even with the best of the best, you can still fall victim to being tracked and collecting malware.
The purpose here isn’t to make you scared of the World Wide Web or even to tell you to stop using it, but instead to make you aware of your own actions online. Staying safe and withholding information will help to stop the release of your personal information.
There should never be a breach where your information becomes public, but companies fall victim to data breaches all of the time. Hopefully, without all of your information as you withhold it.
Protect your computer as much as you can with the tools that are available to you. By doing so, you can prevent hundreds of attacks and feel safe when one of our protection tools pops up a warning box that it has blocked something.
It is best practice to just use common sense on the internet. Stay away from websites that have a bad name, deal with illegal content, or have had bad press in the news for troubled advertisements. If something doesn’t look or feel right, then close out of your browser and search for a new website.
Watch out for downloads and only download content from an official website. For example, Microsoft content should only be downloaded from Microsoft.com, not Microsoftdownloads.com.
Never pay for PC services to a person you do not know and never, ever allow someone to connect or remote control your computer. Once they gain your trust, it’s game over.
I hope that all of this has helped you in staying safe on the internet and given you insight into what it takes to protect just one lone computer browsing the internet.
© 2019 Justin Vendette